Lab 1: Intro to Embedded Security
Lab 1 builds the foundation of frequency-domain embedded security analysis and provides the tool set students need for following labs. It helps students understand the cause and consequence of embedded security problems from a sensor construction perspective, and provides an example of sensor injection attack using intentional electromagnetic interference. It also discusses the defense methodology of administrative physical controls.

Learning Objectives:
- Understand the transformation between different signal representations in time and frequency domains.
- Be able to use hardware and software tools for time and frequency domain signal analysis including oscilloscopes (in Analog Discovery 2), function generators, Matlab/Python, Audacity, etc
- Master the following key concepts: sensor conditioning path, transfer function (frequency response), filtering, resonance frequency, signal injection attack, electromagnetic interference.
Lab 2 | Sound: Acoustic Injection Against Motion Sensors
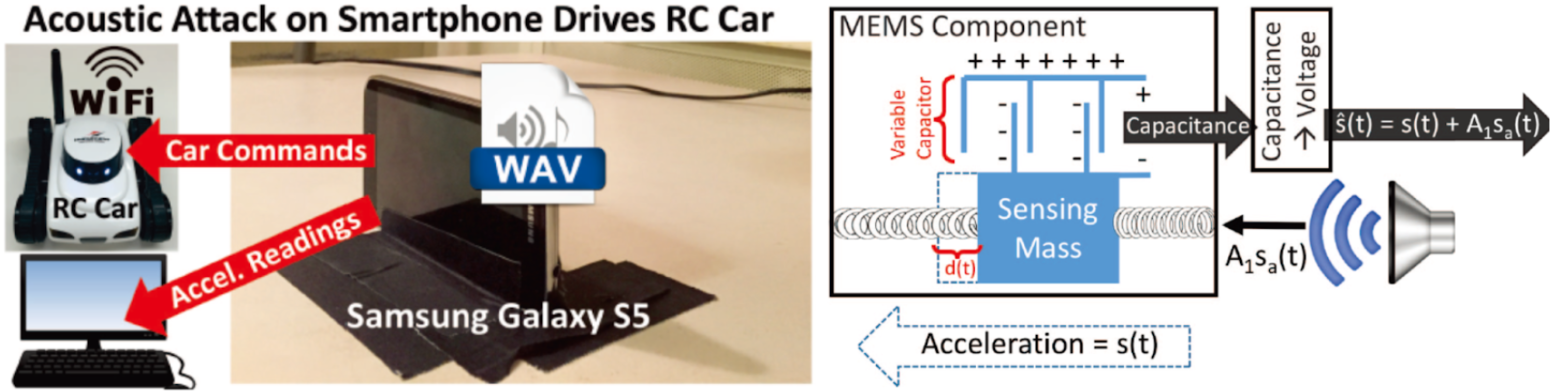
Lab 2 studies the mechanical nature of sound and the embedded security problems caused by sound wave propagation when sound waves induce mechanical resonance in non-acoustic sensor. It investigates the defense methodology of digital and analog filtering.
Learning Objectives:
- Understand the gap between sensor’s intended use/specifications and its physical constructions and how this allows for physical sensor injection attacks.
- Master the concept of mechanical resonance and calculation of signal aliasing. Be able to conduct output biasing attacks against MEMS accelerometers by exploiting aliasing in ADC and using amplitude modulation.
- Understand the practical use of analog low-pass filters and the difference between it and digital filters for defending against the attack.
Lab 3 | Non-linearity: Ultrasonic Injection Against Microphones
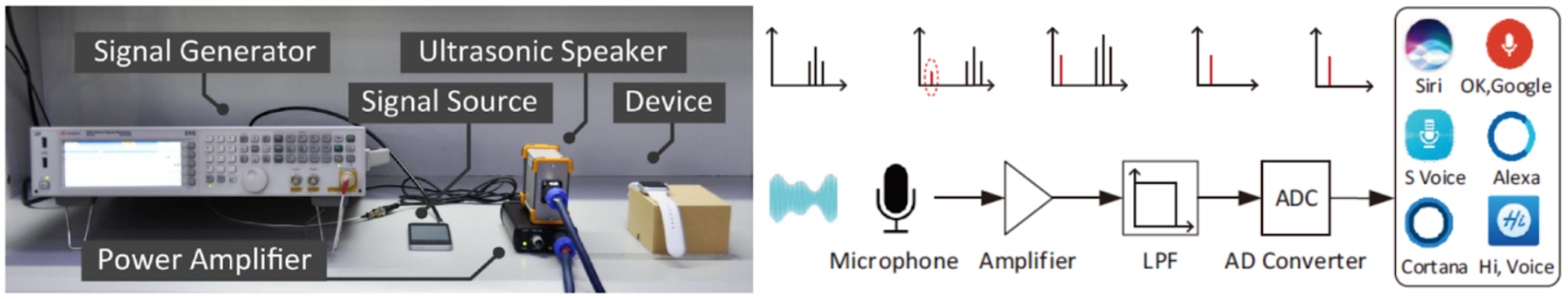
Lab 3 studies the non-linearity nature of sensor conditioning circuits and the attack vectors it exposes for malicious ultrasonic injections to manipulate microphone-based voice assistants. It investiages the defense methodology of anomoly signal detection.
Learning Objectives:
- Understand non-linearity characteristics of sensor circuits and the signal injection modulation scheme based on second-order non-linearity.
- Be able to carry out modulation-based ultrasonic injection attacks using a function generator and portable audio devices.
- Understand the artefacts of ultrasonic injections and the concept and process of leveraging such anomaly signals for attack detection.
Lab 4 | Light: Optical Injection Against Microphones
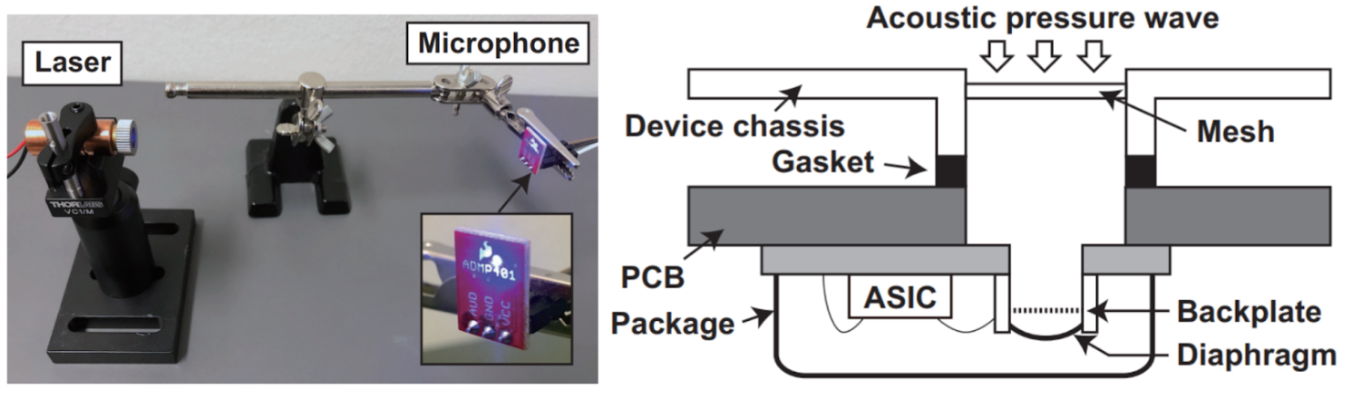
Lab 4 studies the heat-sensitivity and photo-acoustic characteristics of MEMS microphones and the risks that controlled lasers pose against microphone-based voice assistants. It investiages the defense methodology of sensor fusion.
Learning Objectives:
- Understand the physical mechanism that allows MEMS microphones to respond to modulated optical signals and how this property can be exploited for laser-based signal injection attacks.
- Be able to carry out laser injection attacks using a laser diode and audio-modulated signals, and analyze the injection effects using frequency response measurements and signal quality assessments.
- Learn to distinguish laser-induced anomalies from electromagnetic interference, and apply signal processing and anomaly detection techniques to identify and defend against such attacks.
Lab 5: Final Project
The final project takes the form of a tournament that centers on the Light Commands laser attacks against MEMS microphone devices. Students work in teams of 3 or 4. Each team builds a embedded system with voice recognition functionality using the microphone hardware provided. The team then design both the attack and defense techniques into their systems. In the tournament, teams pair up and attack each other's systems in turn.
